Table of Contents
1. How to Host a website in Google Drive with custom Domain
2. Hosting a Website on Google Cloud Platform | Free Hosting
Top
Also on Programming And Computing Page
https://youtu.be/vIJdypOqlL4
I'm going over how to set up and host a website on the free
tier of Google Cloud Platform. Never pay for hosting again
when it can be free!
Here is my complete write up with all commands I used:
http://bit.ly/2N6zFPi
FAQ on Google Cloud Platform Free Tier
http://bit.ly/2qsU89l
3. Asustor AS5202T NAS - Linux Btrfs Blog Posts
Top
Asustor AS5202T NAS Virtual Machine Configuration with VirtualBox
Marc's Public Blog - Linux Btrfs Blog Posts
Top
btrfs Wiki
4. How To Use Raspberry Pi Cameras with Bullseye
5. Raspberry Pi & LoRaWAN Gateway
Top
RAK831 LoRaWAN Gateway with a Raspberry Pi Zero (project) - Playlist
Top
Using blockchain to build trusted LoRaWAN sharing server
Top
Raspberry Pi PCIe Devices
Top
Pi4 USB-C Gadget
Top
NanoPi R4S - OPNsense on ARM
6. N6XRE Tiddlywiki
Top
https://garyrust.github.io/TiddlyWiki5
CLICK
ON PICTURE
N6XRE Tiddlywiki On GitHub - Dokuwiki on Linode
Stalking and Internet Fraud - 333 Crypto - TinyProxy
PDF Documents and Plugin - Kiwix
TinyURL - PureRadioHoland
GMail - BillyMesg - Alexa - The Hidden Enemy - PirateBay - Torrenting Sites - Dokuwiki - 8080 - 73
DuckDuckGo - Ecosia - W3C link checker - Youtube - https://lbry.tv/ - ROKU CHANNEL - Sandbox
PlutoTV - Viki Help - Alexa, Ask web browser search for wikipedia - SpaceX Launch Control Center - USPS
AMAZON - Amazon.com - Contact Us 1-866-216-1072 - ZOHO VAULT - Twitter Zoho Vault - My HealtheVet
Callcentric Click 2 dial -
N6XRE Tiddlywiki -
TiddlyWiki5 on Github -
GitHub Pages
TinyWebGallery Blog
- Anbox Android
Running the Jupyter Notebook -
Midnight Commander Keyboard Shortcuts
- Blender Keyboard Shortcuts
-
SHEEPIT Profile
LXC vs LXD vs Docker – Evolution of the Container Ecosystem -
How to Extract APK File of Any App on Your Android Phone
Learn Enough Docker to be Useful - Blender 2.91 Video - CAD Transforms Movement Basics
Dreamweaver -
Windows 10 Remote Desktop Credentials -
krdc: Access Windows 10 from Ubuntu 20.04 KDE RDP
X2Go Wiki
Yahoo Cryptocurrencies
Testnet Wiki - A Visual Git Reference
7. The Jupyter Notebook - Software
8. Encryption
Top
bup - Very efficient backup system based on the git packfile format - https://github.com/bup/bup
9. Project Gutenberg - AESOP, IN RHYME; OR, OLD FRIENDS IN A NEW DRESS
10. Geek's Lesson channel
11. Talk to Transformer
Top
Transformer replied to - Stalking and Criminal Threats - https://pastebin.com/rXpAfvHV
https://talktotransformer.com/
Intel NCSM2450.DK1 Movidius Neural Compute Stick Amazon Price:$69.99
Movidius NCS + Raspberry Pi 3B+ Youtube - I Ching Online
Top
https://github.com/openai/gpt-2 - Coding TensorFlow Youtube - https://www.tensorflow.org/tutorials
Openai_gpt-2_Language_Models_are_Unsupervised_Multitask_Learners.pdf
How To Set Up Jupyter Notebook with Python 3 on Ubuntu 18.04
This How To Set Up Jupyter Notebook with Python 3 on Ubuntu 18.04.pdf
To access the notebook, open this file in a browser:
file:///home/garyrust/.local/share/jupyter/runtime/nbserver-27409-open.html
Or copy and paste one of these URLs:
http://localhost:8888/?token=ea8815acd4b2ca572ca67530395011b3379741e110f5e7dd
or http://127.0.0.1:8888/?token=ea8815acd4b2ca572ca67530395011b3379741e110f5e7dd
Use the token of your install
Google Colab: An easy way to learn and use TensorFlow - Colaboratory
Learn how to morph faces with a Generative Adversarial Network!
12. PlutoTV
13. Homemade computer chips / integrated circuits
Top
Sam Zeloof channel - Also on Electronics Page
https://www.youtube.com/channel/UC7E8-0Ou69hwScPW1_fQApA
Top
http://sam.zeloof.xyz/first-ic/
14. Mini-Nuclear Reactors Are Coming
15. The Living Universe - Documentary about Consciousness and Reality | Waking Cosmos
16. Deus Ex McKenna ~ Terence McKenna Archive Channel
17. Crime Mapping
Top
https://www.crimemapping.com/map/nv/lasvegas
Top
December’s Most Wanted Malware:
Crypto-Miners Affect 55% of Businesses Worldwide
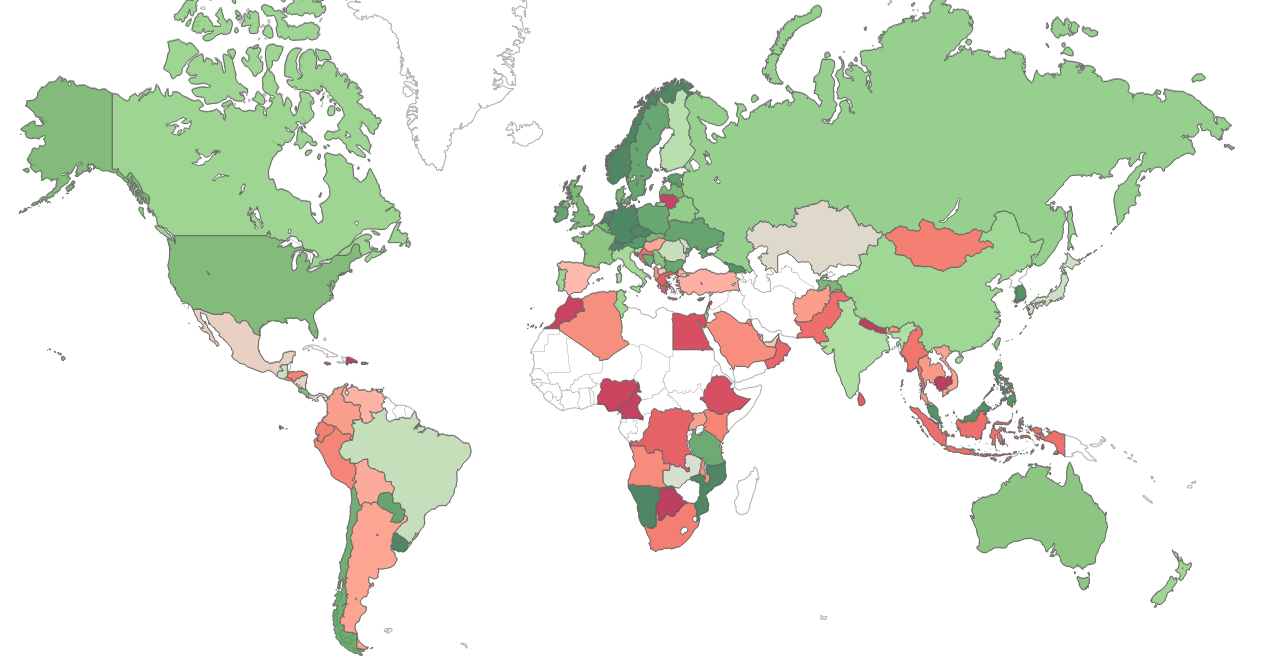
Why I won't work a developer job anymore
https://youtu.be/MbUvTbD9q4A
Selling Wedding dresses in a brick and mortar store is just another jail.
It couldn't be done honestly without going bankrupt. (it's an occult death cult).
Click
18. Stalking and Internet Fraud
Top
Internet Crime Complaint Center (IC3) | Prevention Tips
I'm not trying to cause a problem. Quite the opposite.
Manets are an essential part of security using Ham Radio Repeaters. - IPFS is good for ships at sea.
Compare load times for IPFS - List of human habitation forms and HTTP - List of human habitation forms.
IPFS loads to cache. It takes time to make the P2P connection - but it is like bittorrent, hashed, and secure.
CW - Manet - Firewalls - But how does bitcoin actually work? - Herman Lamm
Also see Internet Ports Blocked or Restricted by Cox and Arp Spoofing below
https://www.fbi.gov/scams-and-safety/common-fraud-schemes/internet-fraud
Top
Click - Talk to Transformer
Top
https://youtu.be/ph8187hyDVA
Top
https://www.youtube.com/playlist?list=PLaVOO-BHQYREFho-Vak2NeBOuaLB153e_
Top
“Any person who willfully threatens to commit a crime which will result in
death or great bodily injury to another person, with the specific intent
that the statement, made verbally, in writing, or by means of an electronic
communication device, is to be taken as a threat, even if there is no intent
of actually carrying it out, which, on its face and under the circumstances
in which it is made, is so unequivocal, unconditional, immediate, and specific
as to convey to the person threatened, a gravity of purpose and an immediate
prospect of execution of the threat, and thereby causes that person reasonably
to be in sustained fear for his or her safety or for his or her immediate
family's safety.”
Top
Stalking and Signal Threats
Cause =⇒ Effect — NEVER Effect =⇒ Cause — ONLY ONE WAY
Faster than Light?
https://en.wikipedia.org/wiki/Racketeer_Influenced_and_Corrupt_Organizations_Act

